
The Evolution Of Data Backup: Is The 3-2-1 Backup Rule A Thing Of The Past?
In today’s digital age, organizations across various industries heavily rely on data for their operations. Whether it’s manufacturing, retail, or service-oriented businesses, the importance of data cannot be overstated. Losing access to critical data can have severe consequences, impacting productivity, decision-making, and even business continuity. That’s why having a backup strategy is essential.
You may have heard a lot about the 3-2-1 backup rule, the “golden backup strategy”, but is it still so up-to-date? Or there are other modern “rules” that can prepare you better for any disaster scenario? Let’s figure it out and dive deeper into what the 3-2-1 backup strategy is, its pros and possible cons, and see if there are any other alternatives to substitute it. But, first, let’s figure out why actually we need a backup…
Table of Contents
- Why do you need backups?
- What is the 3-2-1 backup strategy?
- Are there any limitations to the 3-2-1 backup rule?
- Alternative Backup Approaches
- Backup strategy: how to ensure business continuity?
- Takeaway
Why do you need backups?
There are a lot of situations when you can lose your mission critical data. And, backup is the best practice against data loss. So, what can go wrong with your vital data? Among the main threats, we can mention human errors, accidental or intentional deletion, hardware or software failures, and natural disasters. All these pitfalls underscore the necessity of backups.
Moreover, we shouldn’t forget about compliance with security requirements and international security audits, like ISO 27001 and SOC2 Type II which mandate stringent data protection measures, making backups crucial for meeting regulatory standards and ensuring data integrity during audits.
To be able to withstand any disaster scenario and prevent data loss, you need to create a robust and resilient backup and data protection plan. And the 3-2-1 backup rule is one of those measures that can help you with it.
What is the 3-2-1 backup strategy?
Traditionally, in the context of data backup, the 3-2-1 backup rule has long been regarded as a go-to choice and a widely accepted practice. It emphasizes creating three copies of data, storing them on two different media, and keeping one of them off-site. Thus, by distributing backups across different locations, the risk of simultaneous disasters impacting all copies is significantly reduced. And, as a result, at least one backup copy would remain accessible for restoring your critical data. Sounds nice and secure!
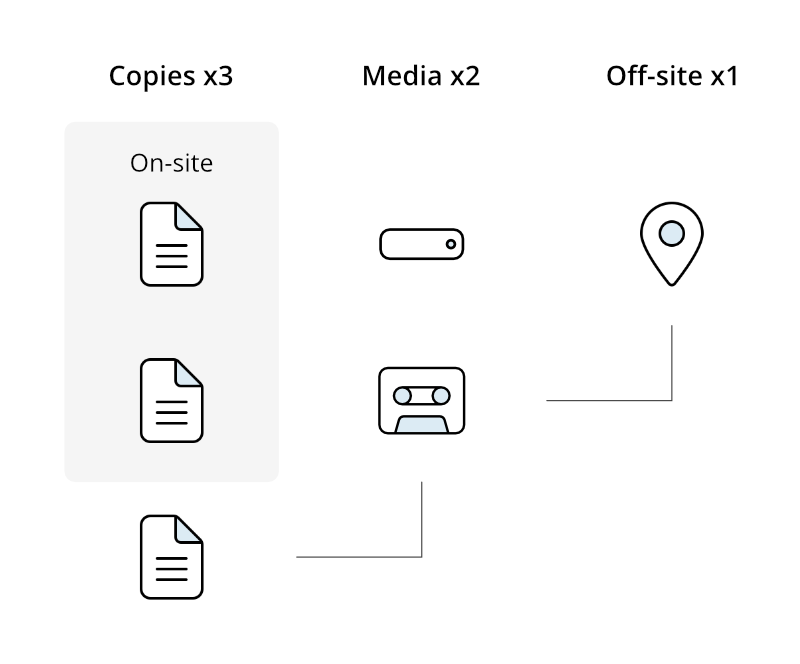
Thus, among the advantages of the 3-2-1 backup strategy, we should mention:
Data redundancy and availability, as even if one of your backup copies becomes inaccessible or corrupted, you always have other copies to rely on.
Protection against hardware failures, as if your primary storage instance fails, you always have copies on different storage devices, including a remote location, to recover data from.
Security against data corruption, as all your copies are stored independently. So, if one of your copies becomes corrupted, you can use another unaffected copy to recover your data.
Resilience to accidental deletions and user errors, as having multiple copies of your data stored in different locations ensures that you can easily recover it once it is deleted or altered.
Protection of ransomware and cyberattacks, as you have off-site backups that aren’t easily accessible to attackers.
Meeting compliance requirements, as many security regulations require the organization to have multiple copies of your data (with data stored off-site) to ensure data integrity and availability.
Fast Disaster Recovery, as in the event of a natural disaster or any other severe disaster that may affect your primary location, you can run your backup from another storage.
Are there any limitations to the 3-2-1 backup rule?
This rule has been serving as a practical guideline and traditional backup strategy for data protection for years. However, the effectiveness of the 3-2-1 backup rule can diminish in the modern era, particularly for small and medium businesses that are heavily reliant on SaaS solutions.
Advancements in technology, increasing data volumes, expanding device ecosystems, the growth of cyber threats, and changes in the business landscape are triggering a re-evaluation of this backup rule. So, let’s take a look at the limitations of the 3-2-1 backup strategy in more detail:
The exponential growth of data and maintaining only three copies might not be sufficient to safeguard valuable information effectively.
The proliferation of devices and endpoints used to access and generate data has made it challenging to ensure comprehensive backup coverage across all platforms.
The increasing sophistication and frequency of cyberattacks, such as ransomware, pose a significant risk to data integrity. The 3-2-1 rule alone may not be able to provide adequate protection against these threats.
The cost of data loss has risen considerably in recent years. Organizations can suffer financial and reputational damage, as well as legal consequences if they fail to adequately protect their data or restore their data fast and meet their Recovery Point Objective or Recovery Time Objective metrics.
Alternative Backup Approaches
Recognizing the limitations of the 3-2-1 rule, organizations are exploring alternative backup approaches that offer enhanced data protection and recovery capabilities. Among the most popular ones are the 4-3-2 backup strategy and the 3-2-1-1-0 backup rule.
The 4-3-2 backup rule
Like the 3-2-1 backup rule, the 4-3-2 backup strategy is designed and intended to provide data redundancy and protection against data loss in any event of failure. The main difference between the mentioned backup rules is that the 4-3-2 backup rule provides an additional copy of your data and a location where to keep your data.
Under this approach, organizations maintain four copies of their data across three different locations, with two of the copies stored off-site.
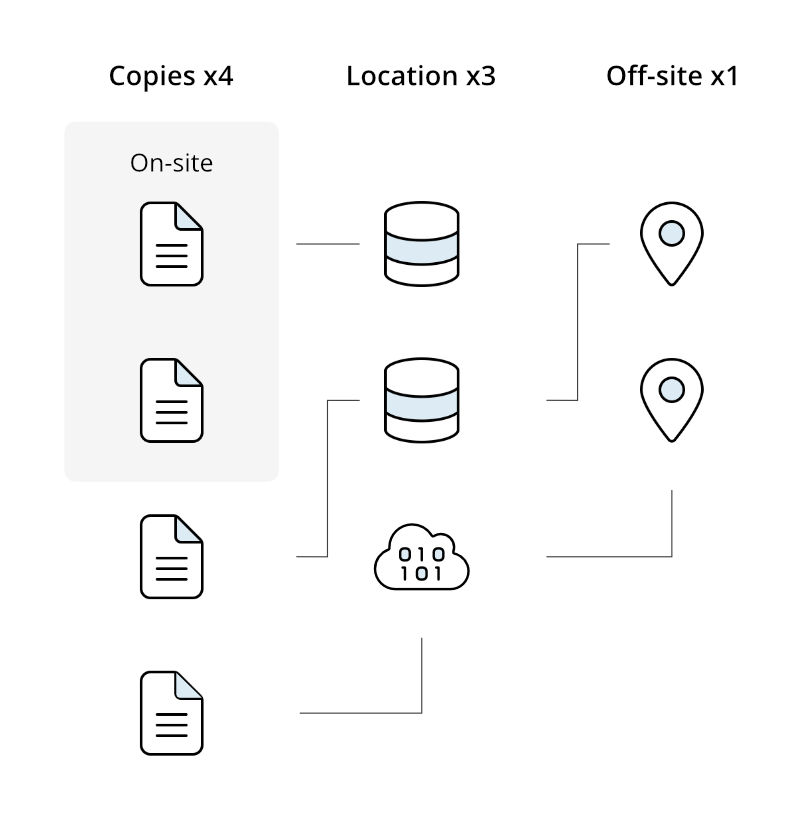
This strategy minimizes the risk of physical storage failures and offers increased protection against random events that could affect multiple locations simultaneously.
The 4-3-2 Backup Rule: how to switch to?
If you want to try and adopt the 4-3-2 backup rule, you should consider the following steps:
Set up a replication plan to create an additional copy of the data.
Ensure the use of immutable storage, which prevents unauthorized modifications to the backup data.
Establish a distributed storage infrastructure across multiple locations to minimize the risk of simultaneous failures.
The 3-2-1-1-0 backup rule
This approach takes data protection a step further by incorporating an offline backup. Moreover, in addition to the three copies, two different media, one of which is off-site (like the 3-2-1 backup strategy), the 3-2-1-1-0 backup rule states that organizations should add an offline backup, which is disconnected from the network after the backup process takes place.
This offline backup can help to mitigate the risk of data encryption or corruption during cyberattacks. The “0” in this rule signifies the importance of backups being regularly checked, verified, and validated, as it ensures their reliability and usability in case of a data loss.
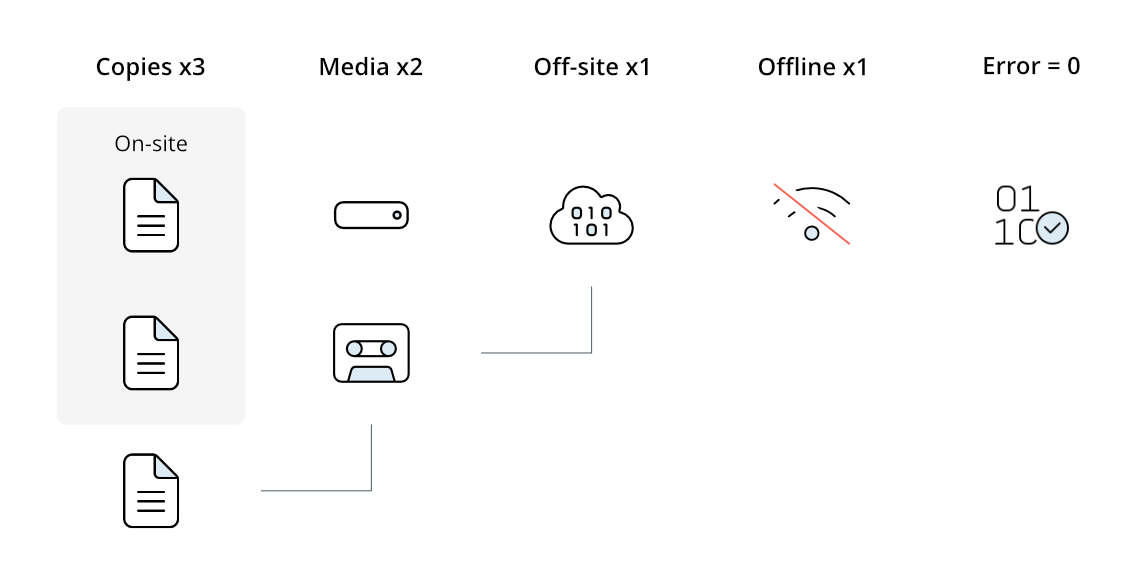
Adopting the 3-2-1-1-0 Backup Rule
Transitioning from the traditional 3-2-1 backup strategy to an alternative backup approach requires careful planning and implementation. Here are the steps you should consider switching to the 3-2-1-1-0 backup rule:
Add another backup copy stored offline, isolated from the network to protect against ransomware attacks.
Conduct regular testing, verification, and validation of backups to ensure their integrity and usability.
Establish clear procedures and documentation for the recovery process, including recreating any data that wasn’t included in the backups.
Backup strategy: how to ensure business continuity?
You can try to build your backup process by yourself enabling some members of your team to perform backups to different storage devices, or you can go for a comprehensive backup solution, like Xopero Software, and implement it into your workflow to protect data.
The third-party backup provider can help you reduce teams’ responsibility and eliminate the consequences of human error. Moreover, comprehensive backup software that provides you with automated backups can help you pass security audits, as reliable backup is one of the necessary measures that those standards require.
Xopero Software can help you meet the 3-2-1 backup rule, as well as the modern ones, the 4-3-2 backup rule or the 3-2-1-1-0 backup rule, as the BaaS provider is a multi-storage system that permits you to back up your copies to different storage media – SMB network shares, local disk resources, or cloud storage. It means that you can add as many data storage instances as your company policy requires.
Let’s look at other features the software solution provides to guarantee that your backup strategy operates within the backup best practices and is resistant to any failure scenario:
Automated scheduled backups which simplifies the process, ensuring regular and reliable data protection without manual intervention.
Immutable storage for keeping your backed-up data secure which eliminates the impact of ransomware spreading in the storage and damaging your original data and copies.
- Replication between storage instances, so that all the backup copies of your data are up-to-date in all your storage devices.
- The possibility of choosing between full, incremental, differential, or forever incremental backups to meet your organizational needs.
- Compression of your backups for saving storage or archiving purposes (to meet compliance regulations).
AES encryption which is considered unbreakable and stands as an additional layer against ransomware.
Disaster Recovery and restore mechanisms, that allow you to quickly restore data and minimize disruptions in the event of data loss or system failures.
Comprehensive monitoring and management that empowers businesses to track backup statuses and verify the integrity of their backed-up data.
Takeaway
To sum up, as organizations increasingly rely on their data, the need for effective backup strategies becomes paramount. While the 3-2-1 backup rule serves as a practical guideline, it is becoming outdated in light of evolving data volumes, device ecosystems, cyber threats, and the cost of data loss. Alternative backup approaches, such as the 4-3-2 rule and the 3-2-1-1-0 rule, offer enhanced protection and recovery capabilities.
Organizations must carefully evaluate their data backup needs and consider leveraging BaaS providers like Xopero Software to ensure comprehensive data protection, compliance, and peace of mind in an increasingly data-driven world. With Xopero Software’s advanced backup solution, organizations can achieve reliable and secure protection for their important data, enabling them to focus on their core business operations with confidence.
Maybe you prefer visual form of learning more? Don’t miss out on our videos on this topic to learn more about the 3-2-1 backup rule and its alternatives:
📌 Why the 3-2-1 backup rule is a thing of the past? Part 1
📌 Why the 3-2-1 backup rule is a thing of the past? Part 2







